-
Notifications
You must be signed in to change notification settings - Fork 575
[User Guide] Core Resources
The core capability of this module deploys the foundations of the conceptual architecture for Azure landing zones, with a focus on the central resource organization.
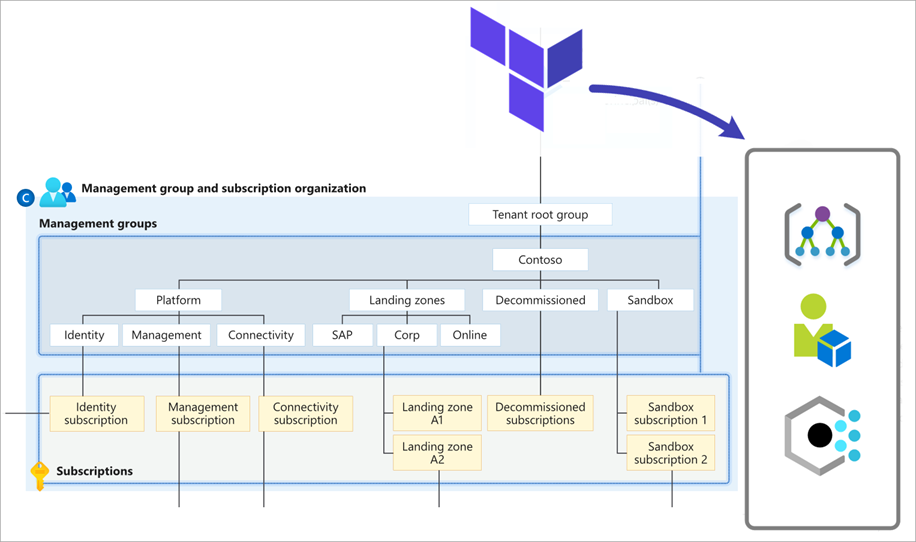
The following resource types are deployed and managed by this module when using the core capabilities:
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Management groups | Microsoft.Management/managementGroups |
azurerm_management_group |
| Management group subscriptions | Microsoft.Management/managementGroups/subscriptions |
azurerm_management_group Or azurerm_management_group_subscription_association
|
| Policy assignments | Microsoft.Authorization/policyAssignments |
azurerm_management_group_policy_assignment |
| Policy definitions | Microsoft.Authorization/policyDefinitions |
azurerm_policy_definition |
| Policy set definitions | Microsoft.Authorization/policySetDefinitions |
azurerm_policy_set_definition |
| Role assignments | Microsoft.Authorization/roleAssignments |
azurerm_role_assignment |
| Role definitions | Microsoft.Authorization/roleDefinitions |
azurerm_role_definition |
The exact number of resources that the module creates depends on the module configuration. For a default configuration, you can expect the module to create approximately 180 resources.
NOTE: None of these resources are deployed at the subscription scope, but Terraform still requires a subscription to establish an authenticated session with Azure. For more information on authenticating with Azure, refer to the Azure Provider: Authenticating to Azure documentation.
Please refer to Deploy Default Configuration for examples showing how to use this capability.
This wiki is being actively developed
If you discover any documentation bugs or would like to request new content, please raise them as an issue or feel free to contribute to the wiki via a pull request. The wiki docs are located in the repository in the docs/wiki/ folder.
- Home
- User guide
- Video guides
-
Examples
- Level 100
- Level 200
-
Level 300
- Deploy multi region networking with custom settings (Hub and Spoke)
- Deploy multi region networking with custom settings (Virtual WAN)
- Deploy with Zero Trust network principles (Hub and Spoke)
- Deploy identity resources with custom settings
- Deploy management resources with custom settings
- Expand built-in archetype definitions
- Create custom policies, initiatives and assignments
- Override module role assignments
- Control policy enforcement mode
- Policy assignments with user assigned managed identities
- Level 400
- Frequently Asked Questions
- Troubleshooting
- Contributing