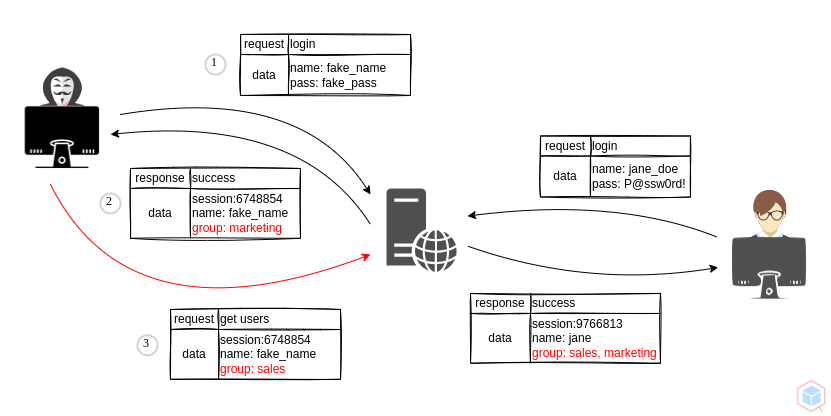
A threat actor may perform unauthorized functions belonging to another user with a similar privileges level.
- Threat actor alters a value that indicates users' group
- Target authorizes adversary to perform functions as if they were part of that group
- Horizontal access control attack
Vary
- Read & modify data
- Execute commands
- Validate access control
- Least privileges
cb8496ab-c8f4-4fda-99a3-37e0b8bc2d55