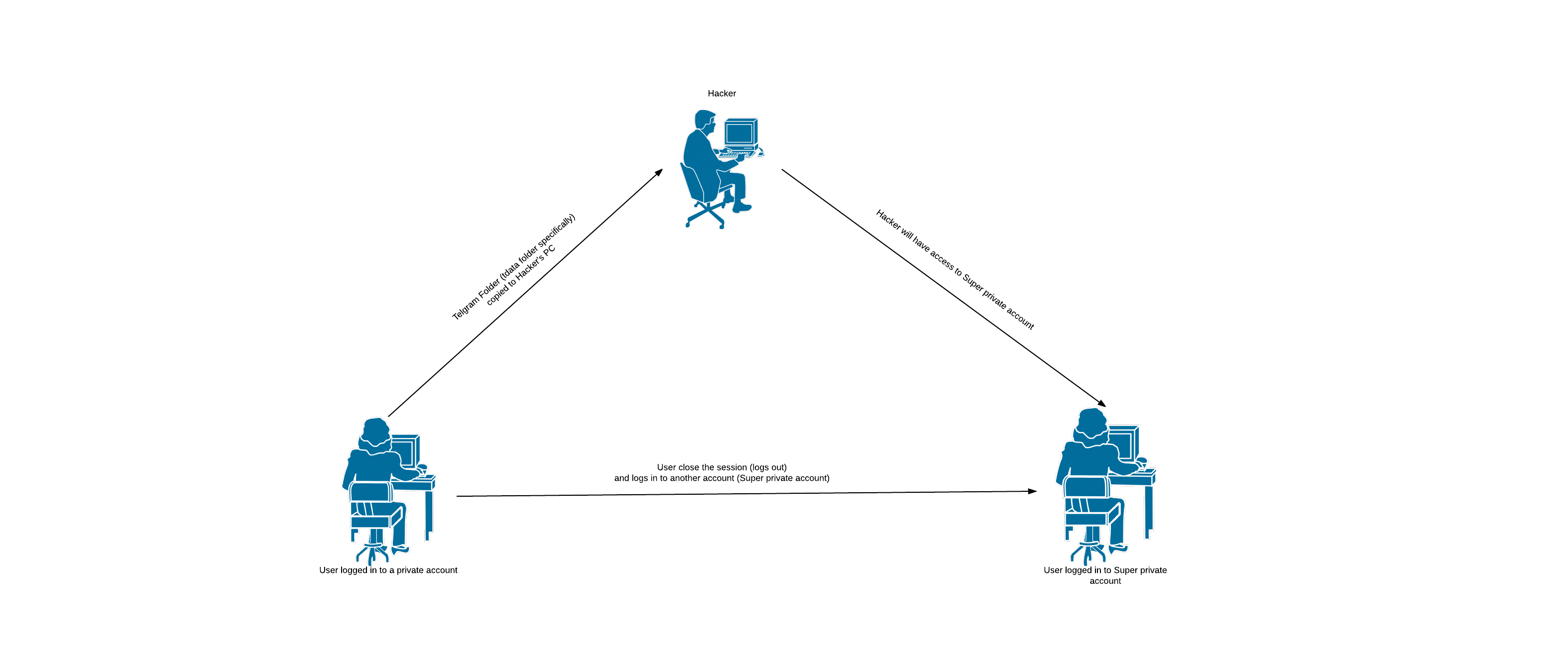
Amidst our researches on Telegram Desktop application, we found a Session Fixation bug, which could lead to full account hijack, alongside with bypassing two-step verification and logging in without any sessions getting recorded.
Telegram Desktop application does not generate a new token for login when an invalid token(not logged in) is there in the tdata folder.
So that if we put an invalid token inside a tdata folder in someone's Telegram folder, our invalid token get's used for login, and we'll be able to hijack his account, without creating any sessions on his account, and off course bypassing two-step verification.
The Session Fixation bug appears on the app because "when a session is closed (or when there is an invalid token there in the tdata), the token assigned to it does get revoked, but doesn't get replaced by a new one, so it gets re-used for the next login".
So that if you do the following steps, you can demo the bug:
- Get a copy of Telegram Desktop application.
- Login to Telegram using one of your accounts.
- Copy the
tdatafolder (or the whole Telegram folder (justtdatamatters)) to somewhere else. - Kill the session you opened in step 2 on another device; so that both Telegram folders are now logged out. (session killed)
- Use the one of Telegram folders (original or copied one) to login to another Telegram account.
- Now if you open the other folder, it will open the same session as the one in step 5.
It IS a bug for sure, and it's a Session Fixation.
Authors: