A tool written in Go that scans files & directories for the Follina exploit (CVE-2022-30190)
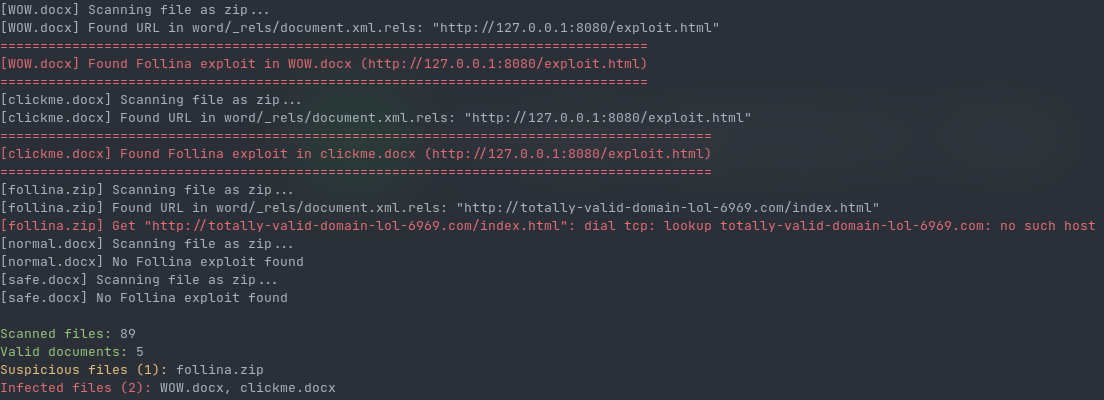 (Note: "Suspicious files" means files that have a URL in them but isn't working)
(Note: "Suspicious files" means files that have a URL in them but isn't working)
git clone https://github.com/ErrorNoInternet/FollinaScanner
cd FollinaScanner
go build# Scan the current directory
./follina-scanner -r .
# Scan a specific file
./follina-scanner amogus.docxUse ./follina-scanner --help for a list of arguments
If you would like to modify or use this repository (including its code) in your own project, please be sure to credit!