-
Notifications
You must be signed in to change notification settings - Fork 39
Home
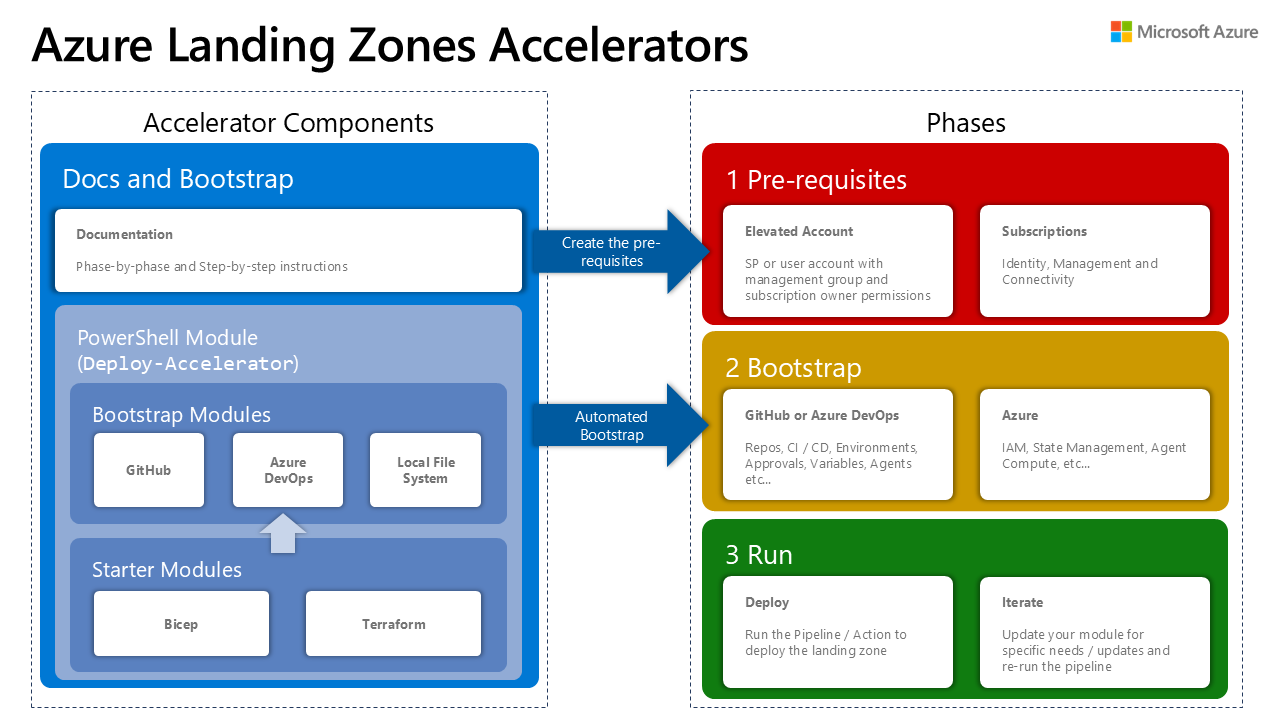
Welcome to the Azure Landing Zones Accelerators for Bicep and Terraform!
The Azure landing zones Terraform and Bicep modules provide an opinionated approach for deploying and managing the core platform capabilities of Azure landing zones architecture using Bicep or Terraform.
This accelerator provides an opinionated approach for configuring and securing those modules in a continuous delivery environment. It has end to end automation for bootstrapping the modules.
The accelerator supports both Azure DevOps and GitHub. We are only able to support the hosted versions of these services.
If you are using self-hosted versions of these services or another VCS, you can still use the accelerator to produce the landing zone code by using the alz_local bootstrap module, but you will need to configure the VCS manually or with your own automation.
The accelerator bootstraps a continuous delivery environment for you. It supports both the Azure DevOps and GitHub version control system (VCS). It uses the ALZ PowerShell module to gather required user input and apply a Terraform module to configure the bootstrap environment.
NOTE: For Bicep users, the accelerator uses Terraform to bootstrap the environment only. Bicep is used to deploy and update the Azure landing zone.
The accelerator follows a 3 phase approach:
- Pre-requisites: Instructions to configure credentials and subscriptions.
- Bootstrap: Run the PowerShell module to generate the continuous delivery environment.
- Run: Update the module (if needed) to suit the needs of your organisation and deploy via continuous delivery.
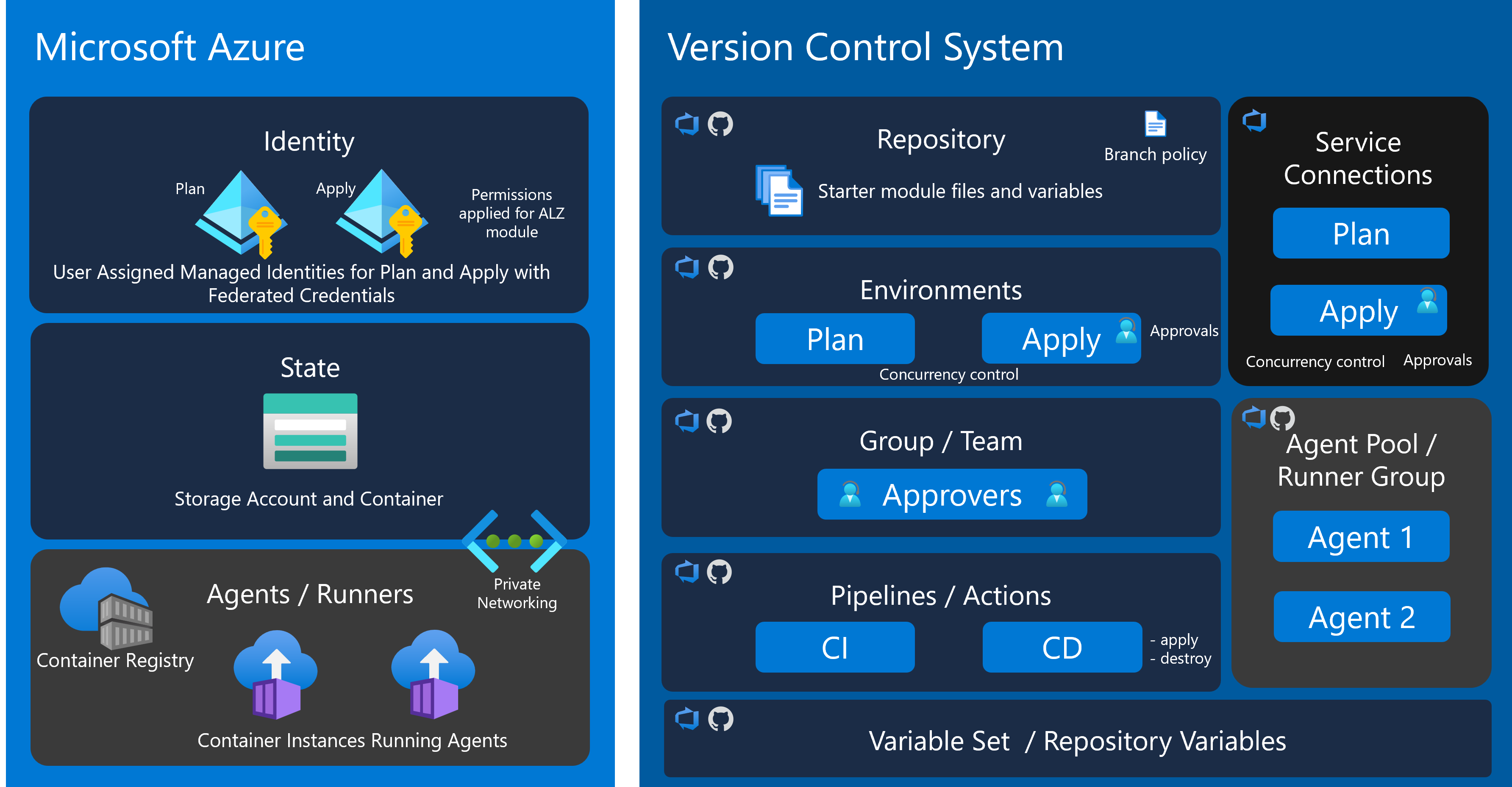
The components of the environment are similar, but differ depending on your choice of VCS:
-
Azure:
- Resource Group for State (Terraform only)
- Storage Account and Container for State (Terraform only)
- Resource Group for Identity
- User Assigned Managed Identities (UAMI) with Federated Credentials for Plan and Apply
- Permissions for the UAMI on state storage container, subscriptions and management groups
- [Optional] Container Registry for GitHub Runner image
- [Optional] Container Instances hosting GitHub Runners
- [Optional] Virtual network, subnets, private DNS zone and private endpoint.
-
GitHub
- Repository for the Module
- Repository for the Action Templates
- Starter Terraform module with tfvars
- Branch policy
- Action for Continuous Integration
- Action for Continuous Delivery
- Environment for Plan
- Environment for Apply
- Action Variables for Backend and Plan / Apply
- Team and Members for Apply Approval
- Customised OIDC Token Subject for governed Actions
- [Optional] Runner Group
-
Azure:
- Resource Group for State (Terraform only)
- Storage Account and Container for State (Terraform only)
- Resource Group for Identity
- User Assigned Managed Identities (UAMI) with Federated Credentials for Plan and Apply
- Permissions for the UAMI on state storage container, subscriptions and management groups
- [Optional] Container Registry for Azure DevOps Agent image
- [Optional] Container Instances hosting Azure DevOps Agents
- [Optional] Virtual network, subnets, private DNS zone and private endpoint.
-
Azure DevOps
- Project (can be supplied or created)
- Repository for the Module
- Repository for the Pipeline Templates
- Starter Terraform module with tfvars
- Branch policy
- Pipeline for Continuous Integration
- Pipeline for Continuous Delivery
- Environment for Plan
- Environment for Apply
- Variable Group for Backend
- Service Connections with Workload identity federation for Plan and Apply
- Service Connection Approvals, Template Validation and Concurrency Control
- Group and Members for Apply Approval
- [Optional] Agent Pool
This outputs the ALZ module files to the file system, so you can apply them manually or with your own VCS / automation.
-
Azure:
- Resource Group for State (Terraform only)
- Storage Account and Container for State (Terraform only)
- Resource Group for Identity
- User Assigned Managed Identities (UAMI) for Plan and Apply
- Permissions for the UAMI on state storage container, subscriptions and management groups
-
Local File System
- Starter module with variables
Check out the User Guide.
The following diagram and links detail the Azure landing zone, but you can learn a lot more about Azure landing zones here.
This wiki is being actively developed
If you discover any documentation bugs or would like to request new content, please raise them as an issue or feel free to contribute to the wiki via a pull request. The wiki docs are located in the repository in the docs/wiki/ folder.

- Home
-
User guide
- Getting started
- Quick Start
- Starter Modules
- Input Files
- Azure DevOps Bicep Complete
- Azure DevOps Terraform Complete Multi Region
- Azure DevOps Terraform Financial Services Industry Landing Zone
- Azure DevOps Terraform Sovereign Landing Zone
- Azure DevOps Terraform Basic
- Azure DevOps Terraform Hub Networking
- Azure DevOps Terraform Complete
- GitHub Bicep Complete
- GitHub Terraform Complete Multi Region
- GitHub Terraform Financial Services Industry Landing Zone
- GitHub Terraform Sovereign Landing Zone
- GitHub Terraform Basic
- GitHub Terraform Hub Networking
- GitHub Terraform Complete
- Local Bicep Complete
- Local Terraform Complete Multi Region
- Local Terraform Financial Services Industry Landing Zone
- Local Terraform Sovereign Landing Zone
- Local Terraform Basic
- Local Terraform Hub Networking
- Local Terraform Complete
- Frequently Asked Questions
- Upgrade Guide
- Advanced Scenarios
- Troubleshooting
- Contributing
